Hello there, today we are going to see, how email spoof check works. Most of you have seen, some emails head over to spam, or some directly, land on your inbox. But how all this stuff, work.
So let's decode it...
I am assuming that you have a mail account and use it actively.
Why I need to know and Learning Outcomes?
Just in case, if you are trying to build something related to emails, it can be a simple automation service or a custom newsletter service. You can use it. Or just if you are curious to learn and know about it.
You will learn the following
- How sending an email works at the server level.
- How the spoof check works in email servers.
- How Gmail has built an UNDO Feature.
Let's Get Started.
Email Verification, works on the concept of DKIM Records.
What are DKIM Records?
In simple words, it is like authentication for mails, which ensures whether the sender is authentic or not.DomainKeys Identified Mail (DKIM) is an authentication standard used to prevent email spoofing. Specifically, DKIM attempts to prevent the spoofing of a domain that's used to deliver email.
So whenever, we send an email with DKIM enabled (automatic if you are using Gmail), the sending server signs the messages with a private key.
If you are having a custom domain, (just like me: abirpal.co ) so being a domain owner of all the emails I send, I have to add a DKIM record, which is a modified TXT record, to the DNS records on sending domain. This TXT record will contain a public key that's used by receiving mail servers to verify a message's signature.
Nowadays, the domain server itself does the same for you automatically, and it just needs only a one-time configuration of the mailing server
So overall, DKIM is a method for verifying whether the sender is authentic or not.
Learning By Doing
Let's see how DKIM verification works, by visualizing when we send an email with the help of the following sequence diagram (Yeah, you might have heard the term sequence diagrams in Software Engineering Classes.)
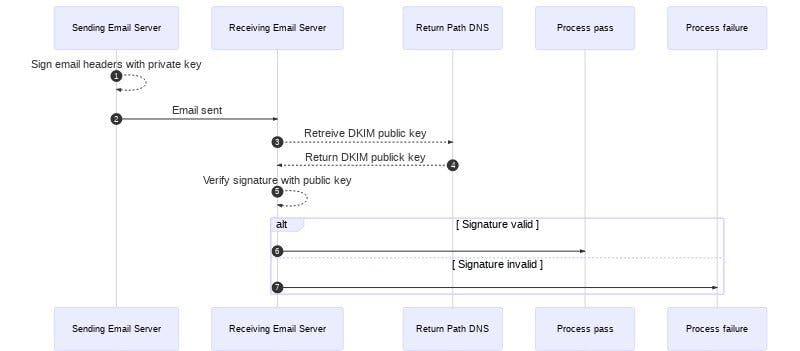
Step 0:
Let's say your mail is: awesome@example.com so, when you hit send, the sending server, signs the email using a private key.
Note: This is the exact time, where Gmail, shows, the undo feature to their users.
Step 1:
So when the mail is sent, the receiving server obtains the DKIM record from the DNS records for example.com or any other custom domain used to send the mail or it can be gmail.com too, if you sent it from your Gmail account.
Step 2:
The receiving server then uses the public key in the DKIM record to verify the message’s signature.
Step 3:
If the DKIM check passes, the receiving server can be confident about the message was sent by the address in the return-path and wasn’t altered in transit.
Note: This is how, email spoofing is checked, by going through DKIM Verification
Step 4:
If the DKIM check fails, the message is likely illegitimate and will be processed using the receiving server’s failure process.
Limitations
While DKIM authentication is an email best practice, it’s important to understand that a DKIM signature is limited in scope. It does not verify the content or tell the receiver to treat the message any differently. Its main purpose is to help verify Sender Identity, which is an important factor (although not the only factor) when it comes to email delivery.

